How SafePassage Works
Explore SafePassage’s zero-storage architecture, dual-mode verification, and real-time compliance controls.


.webp)
Verification Process
Choose between real-time age estimation or full document checks, with instant biometric deletion and built-in fraud protection


Estimates age from facial features

Liveness check to block fake inputs

Stops deepfakes and spoofing attempts
.png)

OCR-based ID validation

Selfie-to-ID face match

Full compliance logs (YC/AML)
.png)

Results returned in real time. All biometric data is instantly and permanently deleted.
Native Emblem Integration
Built-in support for Emblem, the privacy infrastructure powering regulator-approved tokenized verification.

Privacy-First Architecture
Built from the ground up to protect user privacy. No biometric databases, no compliance risk, and no exposure to breach.
Ephemeral Containers
Each request runs in a fresh container that is destroyed instantly. No persistence, no cross-session leakage.
Memory-Only Processing
All biometric data stays in volatile memory and is never written to disk, preventing unauthorized access.
Cryptographic Deletion
Temporary data is encrypted at rest and cryptographically destroyed after use, with zero residue left.
Isolated Compute Nodes
Sandboxed compute flows ensure complete isolation between verification sessions and customer apps.
SafePassage vs Competitors
See how our privacy-first approach compares to traditional verification providers
.png)
.svg)
Built for Global Standards
SafePassage is fully compliant with Ofcom (UK), Arcom (France), KJM (Germany), COPPA (US), and more.
Compliant with leading regulatory bodies in the UK, France, Germany, and more.
Supports region-specific rules — including fallback logic, consent flows, and underage handling.

Real-time logs and verification outcomes with zero stored personal data.

Built to adapt as AV laws expand across Europe, Australia, and the US.
Built to meet global compliance standards
Two verification paths. One compliant system.
AI Age Estimation
Frictionless, low-cost verification using face-based age estimation. Automatically escalates to ID when required by law or risk.
.svg)
No document upload. No user account. Fast conversion.
.svg)
Accepted for low-risk gates under COPPA, KJM, and similar guidelines.




Full Document Verification
ID-backed verification with facial match, fraud checks, and full audit logs. Designed for regulated industries and high-assurance use cases.
.svg)
Government ID check, face match, and liveness. Full-chain validation.
.svg)
Designed for GDPR, KYC, and AML enforcement, with full traceability.




Dual mode verification, built for adaptability
Use AI-based age estimation, ID verification, or both, depending on your flow. SafePassage lets you tailor verification to risk level, user behavior, or jurisdiction — all on a zero-storage, privacy-first architecture.
Frictionless Age
Check
Secure, ID-backed verification

Enterprise-Grade Analytics Without Storing Personal Data
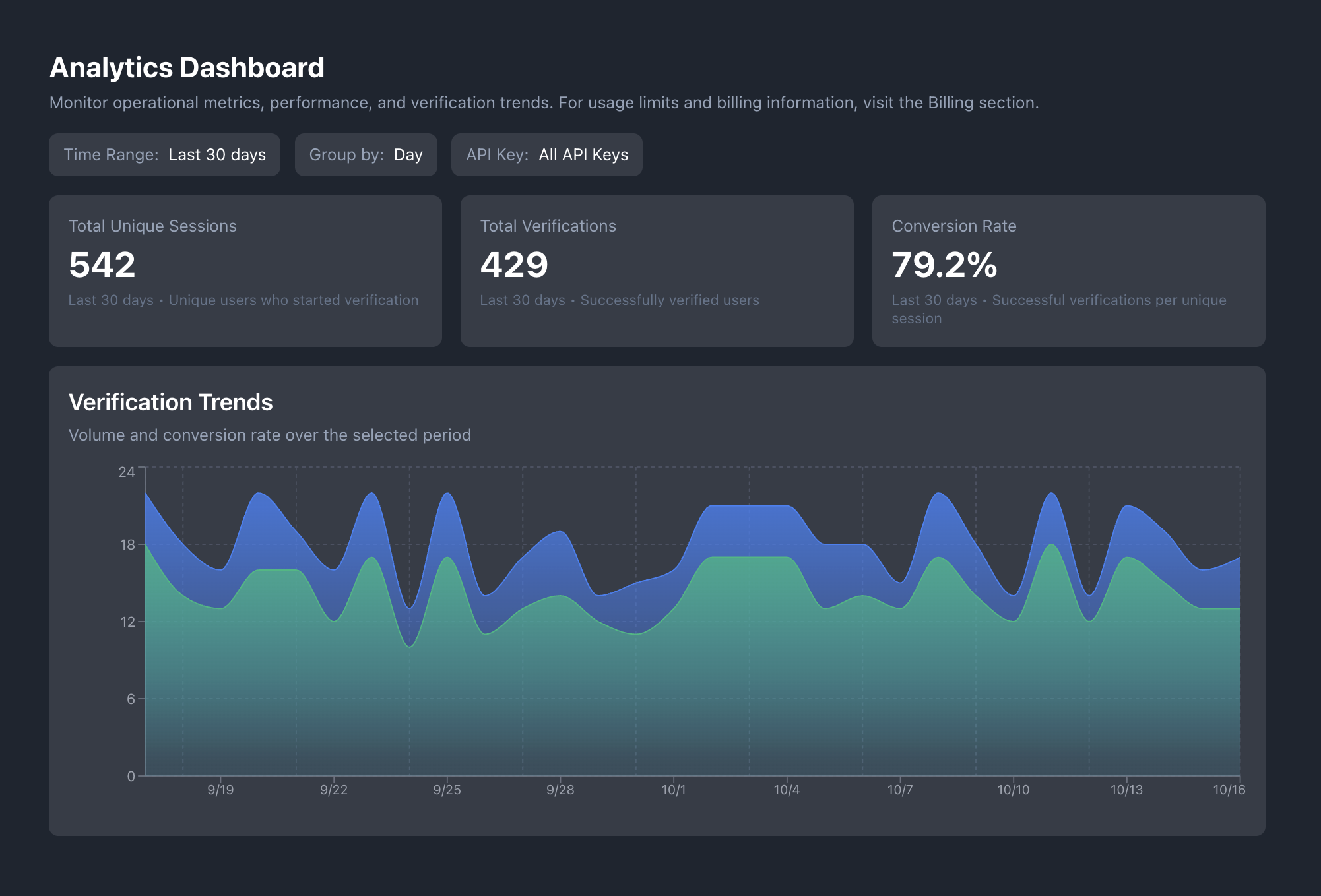
Operational Visibility
See active sessions, live outcomes, and liveness pass/fail events as they happen.

See active sessions, live outcomes, and liveness pass/fail events as they happen.
Compliance & Reporting

Generate audit-ready reports for GDPR, COPPA, KJM, or KYC.

View verification patterns by region to support local compliance requirements.
Fraud & Infrastructure

Detect repeat attempts, device spoofing, and unusual verification behavior.

Monitor latency, uptime, and error rates across your integrations.
Ready to Deploy. Easy to maintain.

Just 17.6KB and framework-agnostic. Works in all major stacks.

Add SafePassage in minutes, not days. Includes full sandbox and test keys.

Encrypted callbacks, tenant isolation, and no data stored on your end.

Adapt the interface to match your platform flow or brand, with full control.

Frequently Asked Questions
Here’s what most teams ask before getting started
We start with L1 (face-based estimation) and escalate to L2 (document-based) only when necessary. This reduces friction and avoids unnecessary data processing.
Yes. You can set rules for when to trigger L2, adjust challenge ages, or apply country-specific verification logic.
Liveness detection, selfie/document cross-checks, and multiple fraud signal checks are standard.
Our L2 flow runs OCR, checks format/security features, and compares document images to the selfie — all in-session, no data stored.
No. All data is processed ephemerally. Nothing — not photos, not ID data — is stored after verification completes.
Absolutely. Use our sandbox tier for free, which includes 100 test verifications with full webhook support and test data.
