Age Verification Without a Trace: How Ephemeral Systems Protect Users
December 1, 2025
The Real Problem Isn’t Verification. It’s Storage.
Most users aren’t scared of verifying their age. They’re scared of what happens next — where their photo goes, who sees it, and whether it ever really gets deleted.
That fear is justified. Traditional age verification tools work like scaled-down surveillance systems:
- Users upload a selfie or ID
- The system stores it “for compliance reasons”
- That data is then available to internal teams, vendors, and sometimes even law enforcement
Even if encrypted, the damage is done. Once stored, data can be exposed to breaches, subpoenas, misuse, or simple mismanagement. For adult content platforms, the stakes are even higher: a single leak can destroy entire lives, not just trust.
The assumption used to be that this was necessary. That verification meant long-term data retention. But that assumption is wrong.
Ephemeral Verification: How It Works
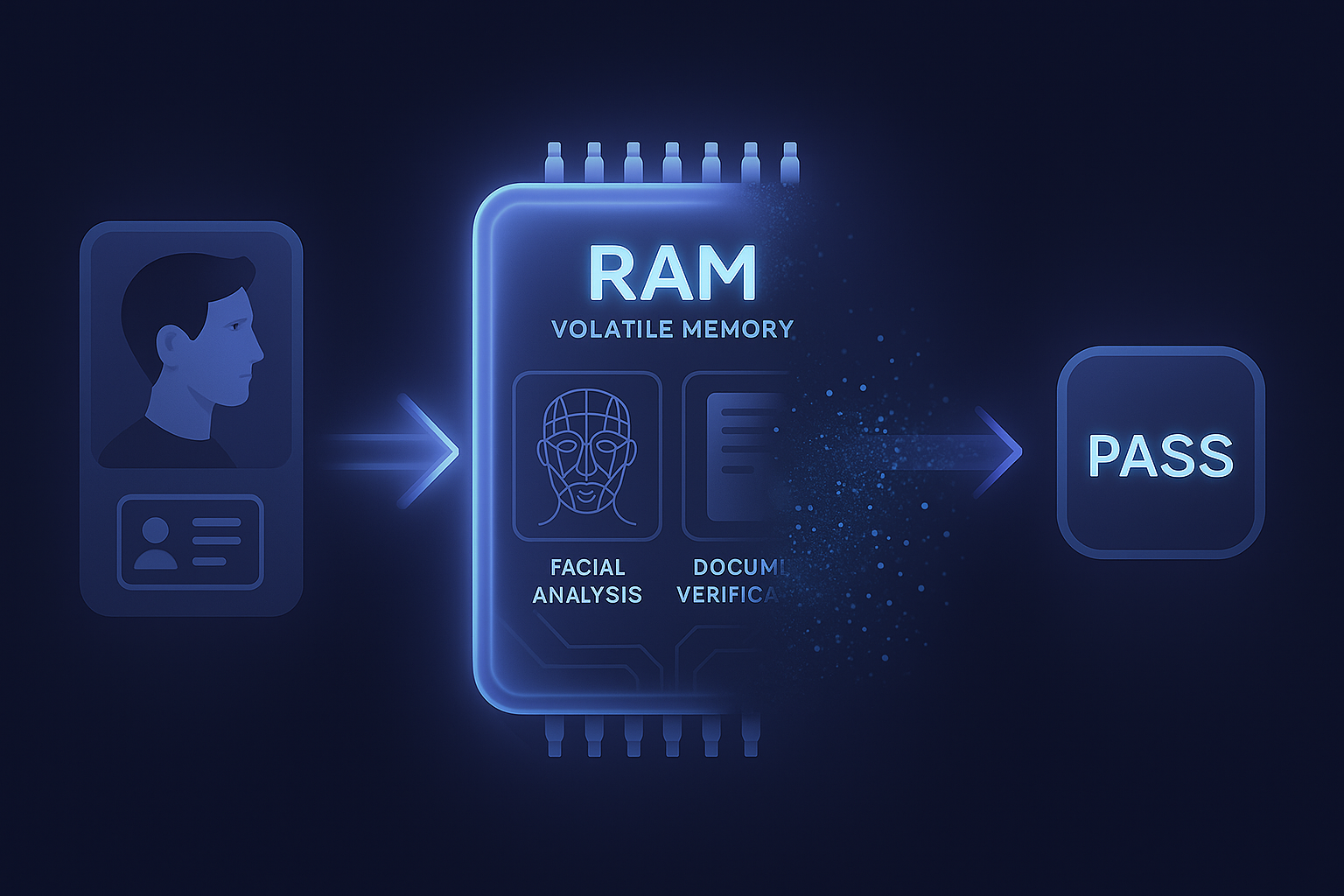
Modern age verification doesn’t require storage, not even temporarily. The best systems now run on a simple principle:
Input → Verify → "Delete" in miliseconds
While we say "delete", in truth, data is never even stored. To illustrate, here’s how an ephemeral, no-storage AV system works:
- User submits a photo or ID
- Data is processed entirely in volatile memory (RAM) — never written to disk, this kind of memory disappears when it’s powered off by default
- The system verifies age using facial estimation or document checks
- Inputs are immediately and irreversibly purged after the result is returned
- Only a pass/fail token is recorded, with no image, no PII, no trace left
This isn’t about short retention windows. It’s about zero retention by design, something that is the cornerstone of trustworthy AV.
With ephemeral AV, users never have to ask:
- Who can access my face scan?
- What vendor is storing my ID?
- What if there's a breach?
- What if the government sends a subpoena?
There’s nothing to leak, share, or subpoena, because the data no longer exists.
That’s the difference between “privacy promises” and privacy architecture.
Users Are Circumventing AV Because They Don’t Trust It
It’s not hard to understand why people use VPNs, spoofing tools, or shared accounts to bypass age checks, especially on adult platforms. They’ve been burned too many times.
- Platforms have been hacked, with stolen passwords littering the entire internet time and time again
- Verification vendors have leaked IDs, exposing the people they were supposed to protect
- Governments have demanded access to verification logs, often without need or just cause
In this climate, users assume the worst, and they’re usually right. Most AV systems still rely on storage, and once a face or ID is stored, it’s exposed to third parties by default.
Ephemeral verification changes that equation. When users know their data won’t be saved — not even for a second — they’re far more likely to opt in rather than work around it.
Good UX, and a Firewall Against Surveillance
If you're building a platform where users access sensitive content, and you’re using a traditional AV provider, you’re effectively running a surveillance node. Maybe not on purpose, but that’s the net result. Ephemeral AV systems are the only real alternative.
They:
- Block underage users without capturing identity
- Operate entirely in-memory, with no trace of who verified
- Prevent platforms from becoming honeypots for regulators, hackers, or third parties
- Deliver audit-ready logs without compromising user privacy
They don’t ask users to trust the system. They make trust technically irrelevant.
SafePassage: Privacy at the Protocol Level
SafePassage was designed from day one to be ephemeral.
- No selfies stored
- No ID scans saved
- No biometric templates retained
- No data written to disk, ever
All processing happens in volatile memory and is deleted immediately after verification. Not minimized. Not encrypted. Gone.
If you’d like to read more about how our verification models work, check out or product page, or jump right into trying SafePassage out. We have a free sandbox option with 100 test verifications, so you can play around with your setup without having to worry about any plans or obligations.
In addition to this, if you’ve enjoyed this content, don’t forget to follow us on X, Bluesky, and LinkekdIn, where we share more articles and best practices each week.
